How many times have you walked out the front door of your house for just a few minutes and not bothered to lock the front door? Probably on more than one occasion, right? What about leaving your car unlocked for just a few minutes — seriously, who’s going to steal your car on a cold rainy morning while you take 2 minutes to grab a hot cup of coffee?
It’s human nature. We rarely worry about managing a potential risk until it’s too late. Once someone breaks into your house, steals your car, or hacks into your WordPress website, then you start to worry.
The problem with all these scenarios is that by the time it happens, it’s too late. You’re left picking up the pieces, cleaning up the mess, and trying to minimize the damage. With just a little bit of planning and prevention, there is a good chance you could have averted the entire situation.
Obviously, this post isn’t about your car or your house, it’s about your WordPress website and the steps you can take to minimize your potential vulnerabilities. The thing is, security begins with having the right attitude. It’s an attitude where prevention and management are at the forefront – not crossing your fingers and hoping that it never happens — because it’s not a case of if your website gets hacked, but when.
Having your website hacked can be anything from a minor headache for a casual blogger, to a major security lapse for a well-established business. If you’re dealing with any kind of private or sensitive information on behalf of customers, a security breach could potentially be devastating to both you and your customers.

WordPress security is a complicated topic, no doubt. This guide should help you navigate through some of the most important issues. The end result being an overall better understanding of how you can manage the risks associated with building a WordPress website — the world’s most popular content management system.
The first step to implementing better security practices comes with understanding and being able to assess the risks you’re facing.
The Truth About WordPress Security Risks
According to W3Techs, use of the WordPress CMS platform accounts for more than 25% of websites worldwide. It’s this figure alone that makes WordPress such a popular target for hackers. Quite simply, there are lots of potential victims to pick from.
The popularity of WordPress has also resulted in an ecosystem that contains over 42,000 plugins — with each one having the potential to open up additional vulnerabilities. And we haven’t even factored in the plugins that are not available from within the WordPress repository.
Hearing these statistics might give you the impression that WordPress is an inherently insecure platform. But your impression would be incorrect. WordPress is actually quite secure. The team at WordPress take security very seriously and have a well-defined process for managing potential vulnerabilities.
With a team of approximately 25 security experts that include both developers and researchers, to say they are proactive would be an understatement. WordPress also works closely with outside security professionals and hosting companies. In addition, where necessary WordPress will collaborate with other teams to resolve vulnerabilities, such as they did with Drupal after shipping version 3.9.2.
In truth, the vast majority of WordPress security vulnerabilities are a result of the thing we love most about WordPress, it’s extensibility. A shortage of highly skilled professionals means that many themes and plugins are released with unknown vulnerabilities or even made available without a pre-release security audit. As a result, they are vulnerable to attack.
Why Would Anyone Want to Hack Your WordPress Website?
As someone who is running a small business website or even a simple blog, you might find yourself wondering, “why me?” Why on earth would a hacker want spend their valuable time trying to hack into your website? It turns out there are a wide variety of reasons that can include:
1 – SEO – If a hacker is able to gain access to your website they can use your site to improve the SEO of another site by inserting back-links. Alternatively, they can insert affiliate links designed to sell something (often of little or no value, as it turns out). Basically, what they are doing here is taking advantage of your website’s good reputation to further their own malicious cause.
2 – SPAM – If you find that you website traffic has all but disappeared in a short period of time, there is a possibility that you site has been hacked for the purpose of sending SPAM email. The result of which is having your website blacklisted. Once a hacker has used and abused your website and hosting account, they simply move on to the next victim, leaving you to clean up the mess.
3 – MALWARE – Malware is a term that refers to malicious software. Hackers love to place malware on other websites because it reduces the likelihood of them being identified as the original source. Malware can do many different things including spying on a user’s actions, keylogging, spreading viruses and more.
4 – THEFT – The average person stores an amazing amount of personal information on their computer: Passwords, credit card information, banking information, and more. Gaining access to your WordPress website can provide a gateway to your personal information and even the information on your visitors’ computers.
5 – ATTACKING OTHER SITES – Sometimes a hacker’s objective is to make a website unavailable to users. These attacks are often referred to as Denial of Service attacks. In order to accomplish their task, hackers will maliciously “recruit” a network of websites to assist in the attack.
Of course, these aren’t the only reasons that a hacker might try to gain access to your WordPress website, but you get a general idea. They may be trying specifically to use your WordPress website for malicious purposes, or they might just be taking advantage of the fact that there is an open door with the potential to lead to an even bigger reward.
Targeted vs Non-Targeted Attacks
Before we jump into discussing specific preventative measures, it’s valuable to understand the two primary types of attacks that occur against WordPress websites:
The first type of attack we’ll discuss is not personal, meaning the attacker is not specifically out to get you or your business. These are what you call non-targeted — automated attacks that look for a way to take advantage of a known vulnerability. Many hackers are inherently lazy (or smart, depending upon how you look at the situation). They use automated tools that are capable of scanning a wide range of IP addresses, for example, all the websites located on a particular shared hosting server.
When they scan a range of IP addresses, the tool they use is looking for a specific version or WordPress or a plugin that indicates a potentially exploitable vulnerability.
We’ll cover some of the specific ways you can deter against non-targeted attacks in just a few moments, but first let’s talk about something a little more personal: Targeted attacks.
A targeted attack happens when a hacker makes a conscious decision to target your website. The law of attraction dictates that the more popular your website becomes, the more likely it is to be targeted. There’s a good chance you won’t even know why it’s being targeted. What matters is that it’s happening and you need to find a way to mitigate damage and then prevent it from happening again in the future.
Two examples of targeted attacks would be the recent and well-publicized attack against Ashley Madison and the attack that occurred against the Smart Passive Income Blog back in 2013. Both of these targeted attacks resulted in considerable damage in terms finances. In the Ashley Madison example, there were several instances where police reported a loss of life as a result of sensitive information being released.
There is not much you can do to prevent a targeted attack from occurring. What you can do is harden your site to the make the process as challenging as possible for a hacker. Then, cross your fingers that they’ll move on to an easier target.
Understanding Common WordPress Security Vulnerabilities
At the forefront of web application security is OWASP (Open Web Application Security Project) — a non-profit organization that is responsible for improving software security around the world. OWASP also produces a document called the OWASP Top 10 that is designed to summarize the most exploitable security flaws across a wide variety of web applications.

Ideally, any time a plugin or theme is released, the developer will have given consideration to the list of vulnerabilities published by the OWASP in an effort to make sure their code is secure.
As you can imagine, this is the best case scenario, and not every developer takes the time to consider the vulnerabilities contained in the document. They may not even have the skill required to do so.
In the event that a theme or plugin is released with security vulnerabilities, the WordPress security team will make an attempt to notify the developer and help them repair the vulnerabilities. In situations where this isn’t possible or the vulnerability is serious, the security team has been known to remove the theme or plugin from the repository and patch it themselves.
Next, let’s take a look at the actual OWASP Top 10. Keep in mind that most of the vulnerabilities in the top ten list can be tied back WordPress in one way or another — we’ll cover two of them in greater detail as an example.
The OWASP Top 10
- A1 – Injection
- A2 – Broken Authentication and Session Management
- A3 – Cross-Site Scripting XSS
- A4 – Insecure Direct Object References
- A5 – Security Misconfiguration
- A6 – Sensitive Data Exposure
- A7 – Missing Function Level Access Control
- A8 – Cross-Site Request Forgery
- A9 – Using Components with Known Vulnerabilities
- A10 – Unvalidated Redirects and Forwards
A1 Injection
WordPress uses SQL to communicate with your database which in turn makes it vulnerable to SQL Injection Attacks. For example, a malicious statement designed to extract sensitive information from a database can be entered into a form field. This process might be handled manually but a hacker can also automate the process using a tool like Burp Suite — which, ironically, is also a tool that security professionals use to test for security vulnerabilities.
A hacker can progress from generating a simple error message in an input field to extracting a list of user accounts contained in a database. Obviously, this is a simplified explanation, but it goes to show how a small vulnerability can lead to the release of sensitive information. SQL injection attacks are one of the top vulnerabilities facing the WordPress ecosystem.
A3 Cross-Site Scripting (XSS)
XSS vulnerabilities are extremely common and equally complicated — there are several variations of XSS attacks such as reflective, and persistent, which we won’t go into detail about here. However, we should, at least, cover the basics as they relate to WordPress.
Taking advantage of an XSS Vulnerability requires two innocent parties. First, a vulnerable WordPress website is needed, and second an unwilling visitor. Essentially what happens is that when a hacker finds a vulnerable website they distribute malicious scripts (via email for example). When a user clicks on the link containing the malicious script it directs them to the vulnerable website. The website then reflects the script back to the visitors browser where it is executed willingly because it came from what was believed to be a safe website.
A malicious script can perform a wide variety of activities. Some examples are:
- Stealing session credentials.
- Replacing the form action for a login screen so that when you click submit, your login details are sent to the hacker instead of logging you into the website.
- Capturing keystrokes and sending them back to a hacker.
XSS vulnerabilities have been reported and fixed in many well-known plugins including:
This list represents a tiny fraction of plugins that have experienced problems. But even from this list of well-known plugins, you can imagine how many millions of users were potentially affected. Keep in mind that hackers aren’t always the first to discover the vulnerabilities. In many situations, the good guys uncover the vulnerability first and provide a patch before a more serious problem develops.
How to Manage WordPress Security
If you’ve taken the time to read through the first part of this article, give yourself a pat on the back. Although it’s a very basic overview, you probably have a greater understanding of WordPress vulnerabilities — both the types and potential risks — than most people who are using the platform on a daily basis.
That’s really only one-half of the puzzle through, right? Now that you have a better understanding of the risks, what actions can you take to minimize that risk?
The first thing you need to understand is that there is no such thing as a WordPress website that’s 100% secure. Oftentimes, the best approach is to protect your site against the largest and most common threats. Remember the house and car analogies that we mentioned in our introduction? Sometimes just locking the door is half the battle. But where do you start?
We reached out to Tony Perez of Sucuri and asked about the top security threats that a small business owner running WordPress needs to be concerned about for 2016 and beyond. If you want to hear it straight from someone who knows exactly what they are talking about, here’s what Tony had to say:
Beyond is a very big term, especially when talking about security as it’s a constantly evolving animal. With that in mind, what I’d say about security in WordPress is that the attack vector has been pretty consistent for the past two years. It’s revolved around two very distinct vectors – Access Control and Software Vulnerabilities.
Access control being how the environment is logged into – think wp-admin in WordPress, but think beyond that to access to servers and hosting accounts. Access is a huge factor, and often what we hear being exploited (i.e., attacked) when you hear of things like Brute Force attacks.
Software vulnerabilities, specifically the exploitation of said vulnerabilities, is and continues to be a big problem for WordPress users. Not because of the platform itself, but because of its extensibility and the plethora of plugins / themes available, and the shortage of skilled professionals, relative to the adoption of the platform.
There is a new player, to Content Management System / Consumer websites, though, that I think will start growing in the coming year(s), and that is attacks against the availability of websites (WordPress and others).
As platforms continue to strengthen their development practices, it becomes increasingly more difficult to exploit environments, it’s a natural progression. The one thing that continues to be attacked, however, with little effort — relatively speaking, is the availability of a website. These attacks will come in the form of Denial of Service and Distributed Denial of Service attacks.
How to Harden Your WordPress Website
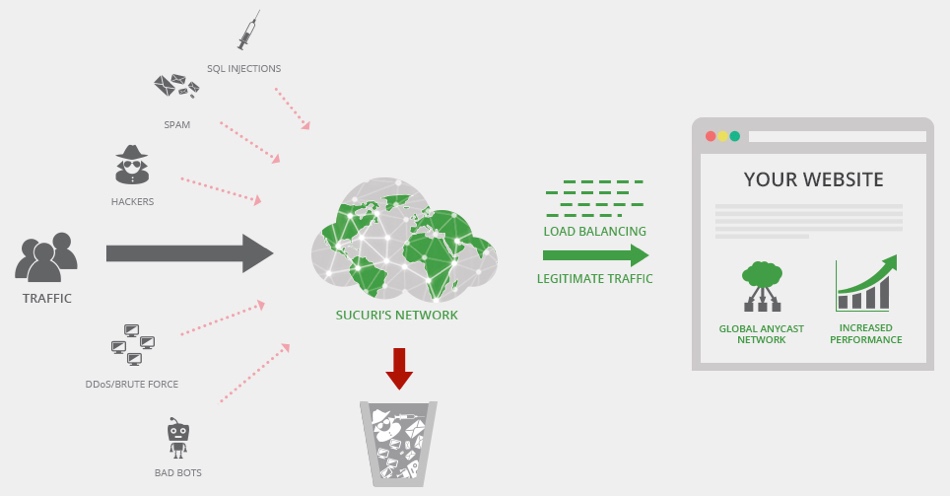
While the purpose of this article is not to review WordPress security plugins or services, we still want to give you some actionable ideas. The reason so many people end up having their WordPress website hacked is because they fail to take any preventative action until it’s too late.
We thought this would be a great time to get some feedback from another expert in WordPress security, so we asked Robert Abela at WP White Security, “What do you think are the top 2-3 security mistakes that WordPress users make when maintaining their websites?”
Without hesitation he answered:
There are many security mistakes one can make, and in WordPress’ case, it all boils down to lack of experience in maintaining websites. Just because it is easy to use, it does not mean it is easy to maintain, especially from the security point of view. And because of lack of experience people:
- Use weak usernames and passwords.
- Fail to keep software up to date (be it WordPress core, plugins, themes, the web server, or the software on their own computer).
- Install plugins and themes without doing any basic research about them, or checking the source.
Keeping those three items in mind here are several tips that can help you improve your overall security posture. This is by no means an inclusive list. There are many more actions you can take to further harden your security. But if you pick a handful of the ones below, you’ll be ahead of 90% of the other WordPress sites out there.
1. Back-up Your Website
Above everything else, the most important thing you can do is to backup your website on a regular basis. If you’re using WordPress (or any platform for that matter), it’s not a question of if, but when your website will be hacked. When it happens, the first place you turn in an effort to get things back to normal is your backup.
There are a variety of ways that you can backup your website – some hosting companies provide automated backups of you could even use a plugin like Backup Buddy or a service like VaultPress.
2. Pick a Solid WordPress Host
Picking a solid, reliable hosting company for your WordPress website can go a long way towards relieving some of your security worries. Hosting companies need to take security seriously, but this is not to say that you must rely on a managed WordPress hosting company. There are lots of great hosting companies to pick from with a wide variety of price points.
As an example of proactive security practices, some hosting companies will automatically block an IP address after too many failed attempts to log in or access a hosting account. You should also make sure that they are using a recent version of MySQL and PHP, two of the components that are vital to WordPress. Never hesitate to ask your hosting company for more information on their security posture.
3. Use Reputable Themes and Plugins
Choosing reputable themes and plugins is an essential step in reducing the overall surface area available to potential hackers. Many of the top WordPress plugin or theme developers request a third-party audit from a company like Sucuri prior to release.
If you look back to the section where we discussed XSS vulnerabilities, it’s clear that vulnerabilities can be present even in well-established themes or plugins. The difference being that reputable or well-established theme companies or plugin developers are more likely to be proactive in their approach to security.
On the topic of plugins, it’s also a good idea to limit your total number of plugins to as few as possible. More plugins, by default, mean you are providing a greater potential attack surface.
4. Use a Strong Username & Password
Not only is this one of the issues brought up by Robert from WP White Security, it goes without saying that you need to make access to all of your accounts as difficult as possible. Use unique, and difficult to guess usernames and passwords across all your accounts, not just your WordPress login. You should also implement two-factor authentication on any account that provides the option and using a plugin like Clef Two-Factor Authentication for your WordPress site
Consider for a second the damage that a hacker could inflict if they gained access to your domain registrar, hosting account or cPanel. Despite these risks, many people insist on using the same login credentials across multiple accounts. A sign of a strong password is one that you can’t remember, but services like LastPass or 1Password are designed to manage that for you.
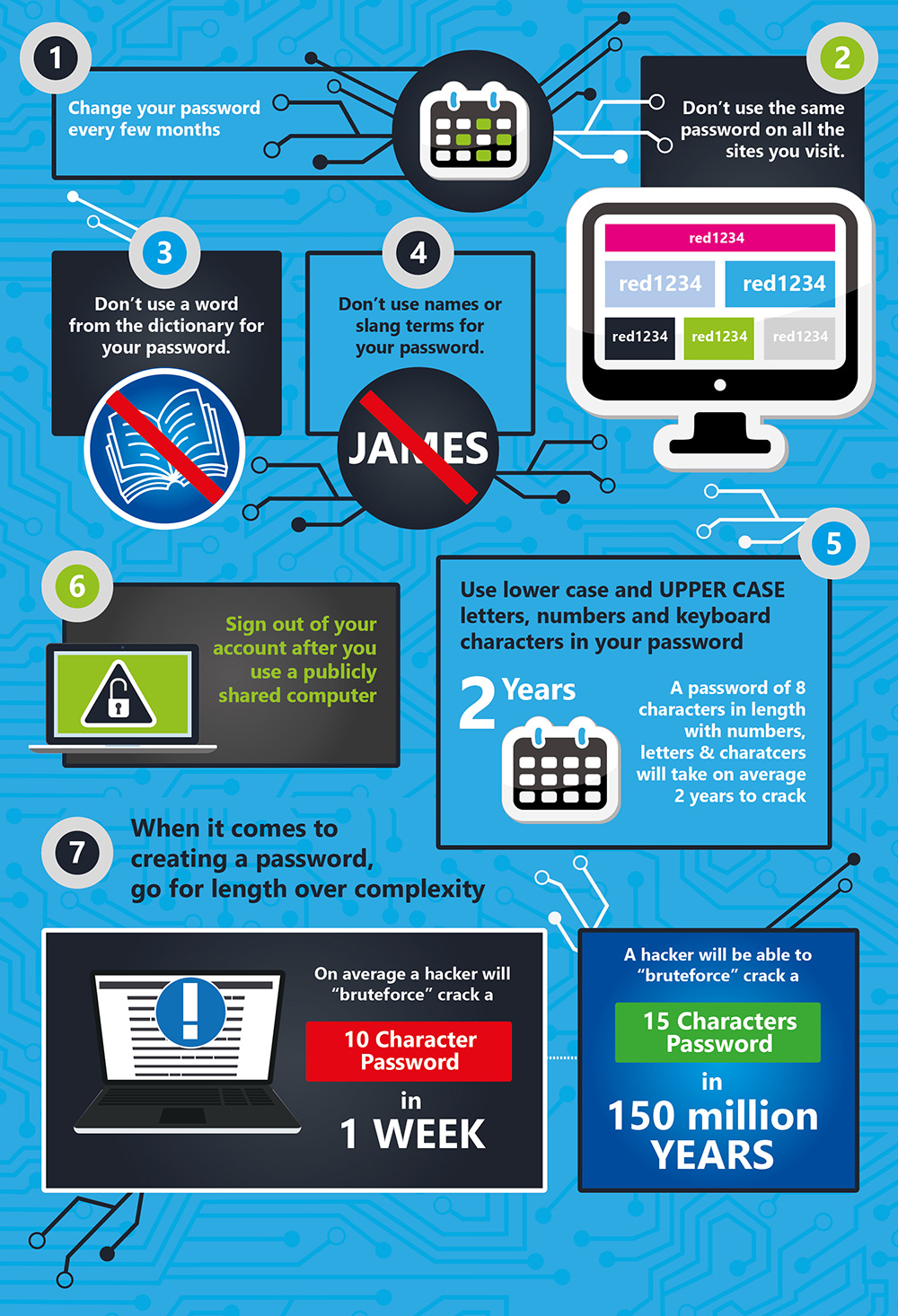
Here is some handy advice for creating strong passwords:
4. Limit Access to Vital Parts of Your WordPress Website
Making it more difficult for a hacker to access specific parts or your WordPress installation, is a great deterrence. You can also achieve some of these objectives by using a security plugin, which we’ll cover next. In case you’re interested in completing the process manually here are a few actions you can take:
- Secure your wp-config.php file by moving it one directory above your WordPress installation.
- Make sure your directories and files have the correct permissions.
- Disable the File Editor in the WordPress Admin panel which means a hacker will require FTP access to access core and theme files.
Limiting access also includes the use of appropriate user roles. This is especially important when you have more than one person working on your website. For example, if you have employees, authors, editors or anyone else accessing your WordPress website, you should provide them with their own login credentials that are appropriate for the work they are doing. Don’t assign an administrator role unless a person actually requires admin functionality.
5. Use a Security Plugin
Many users find it easier to rely on a one-stop security solution. If that sounds like you, one of the available WordPress security plugins might be suitable. Here are a some of the popular options:
iThemes Security – available in both a free and premium version, iThemes provides over 30 different ways to improve the security of your website.
WordFence – is another security plugin that offers both a free and premium version. With just over 11 million downloads, WordFence has a strong user base who depend on this plugin for their security needs.
Sucuri – While Sucuri maintains a free plugin in the WordPress repository, they also provide a more comprehensive service that includes: malware and blacklist scanning, DDoS protection, malware cleanup, firewall protection and more. One of the great features of the Sucuri service is that it includes cleanup in the event that you site is compromised.
Here are a list of other Malware scanning tools for WordPress.
6. Monitor What’s Happening on Your Website
Keeping an eye on what’s happening with your website can provide important clues that something might not be right. There are a few different places you should check on a regular basis.
- Your analytics can provide key information about your website traffic. Any sudden change, especially a sudden drop might indicate a problem
- Perform a site search using site:http://yourdomain.com – Are there any sudden or negative changes in the number of pages indexed? Are all your meta descriptions appropriate?
- What are the other logged in users on your website up to, authorized or not? Anytime someone accesses the backend of your WordPress website you can use a plugin like WP Security Audit Log to track what’s happening.

CyberScanner is a new website vulnerability scanner created by a team of website security experts. Currently it checks for over 98000 different vulnerabilities. It’s very easy to setup and every week you’ll receive a security audit report which is great for GDPR compliance.
The point here is that you should be vigilant. You can potentially avert untold damage by catching a security breach as early as possible.
What To Do if Your Website is Hacked
In the unfortunate event that your WordPress website is hacked, you’ll breathe a sigh of relief knowing that you have a recent backup on hand. But what is the ideal course of action for a typical WordPress administrator?
To answer that question we again asked Robert Abela of WP White Security and he recommended 3 steps:
- Make a backup of what there is. This will come in handy to analyze what has happened. Be sure you’re not overwriting a previous, uncompromised version of your website.
- Restore a backup and change all passwords.
- Analyze the backups, logs and everything else to see which vulnerability was exploited so you can close it down in the restored version of your website.
He also added that although malware is sometimes easy to find and remove, most of the time you will need professional help.
Final Thoughts on Hardening Your WordPress Security
WordPress security and more specifically the hardening of your website is something you can choose to ignore at your own peril. As the most popular CMS in the World, WordPress is the target of innumerable hackers.
Even if you feel that your website or small business is too small to be a target, you need to remember that a large percentage of attacks are automated and not specifically directed at your website. If you are interested in digging into some hard numbers, Impervia produces an annual Web Application Attack Report that contains some frightening statistics.
Despite what feels like doom and gloom, the best decision you can make is to be proactive with your WordPress security posture. Too many WordPress administrators do too little, too late. Even though no WordPress website can ever be 100% secure, any action you take today to harden your security can pay instant dividends.
Jamie Spencer
Latest posts by Jamie Spencer (see all)
- How to Start a Successful Cryptocurrency Website - September 12, 2024
- 50+ Ways To Advertise Your Business For Free On The Internet – 2024 Guide - September 5, 2024
- The Fastest WordPress Hosting Providers 2024 – If You’re Not Fast…You’re Last!!! - July 8, 2024

Hi Joe,
Indeed a great list of common WordPress security mistakes.
A couple of days back I faced a situation where there was some unwanted ads being displayed on my blog and that was something I did not install. When inspected I found that there was a lot of unwanted codes that were injected into the WordPress theme files and other main files.
On further inspection I found out the following 3 things which were the reasons for this:
1). Not updating the other WordPress installation, plugins and themes that are being run from the same hosting account if you are using a shared hosting
.
2). Optimizepress 1.0 is known to have a security issue and they have released an update to it. This doesn’t update in the normal updates from your wordpress dashboard. You might want to update it manually, if you haven’t done it yet.
3). Not Cleaning and optimizing your database periodically
4). Leaving the default themes like twentyeleven etc. as it is and not updating them. This primarily happens if you are using a different theme and these default themes just remain there.
5). Not uninstalling plugins that haven’t been updated for a long time by its creators.
These are prone to attacks. A couple of solutions that I found was installing plugin like Wordfence or, Bullet Proof Security or, Better WP security.
Hey Jamie,
The use of some HTTP headers, as for example X-Frame-Options and X-XSS-Protection, will provide an additional level of security to your WordPress blog. See https://zinoui.com/blog/http-headers-for-wordpress
Cheers,
Very thoughtful and helpful article.
I had to deal with my websites’ being hacked. The worst part of all of it, I had very little help from the “technical support” of my hosting provider, as well as the over three-week turn-around time to answer my support requests!
Anyway,
I do a lot of my coding, design, and development on XAMPP at home. This is also where I have been developing some sound and secure .htaccess-directives for locking down my websites. I must stress that having a very good, responsible web-hosting provider means all the difference. Otherwise, even the best security you may put in place will probably not mean much in terms of positive results. The permissions attributes of files and folders is a very important consideration. Many good hosting companies will have forums and discussion boards that are loaded with great security-related advice.
I have noticed that a lot of websites are also using CloudFlare, which seems to help considerably against DoS and DDoS-type attacks. I did notice that my websites had experienced a lot of DDoS-attempts, as well as other methods of “probing”. So, keeping track of web-traffic on your site(s) is VERY IMPORTANT. This is where you may get early warning that things are happening to your website(s).
As to the use of plugins:
You should only install and use as many plugins as you actually need! Not very many WordPress sites need ALL OF THEM! Good security plugins should be considered a MUST for any serious website owner/admin. It is a shame that WordPress does not have login-attempts limiting built in. Therefore, a good plugin to guard against brute-force-type attacks against your website login function is also a must..
I saw another good idea, in relation to WordPress website security:
Check your WordPress installation(s) with WP-Scan. This would give a basic idea of how well you properly configured your site security, and how your (hopefully) up-to-date plugins and themes fare as far as security. It also helps if you incorporate (perhaps, into your custom themes) into your “function.php”-file, a few WordPress filters to remove the version-number-tagging that is embedded into the link-url markups in the displayed pages. – Why would the world need to know what versions of software you are running your website with?
So yes, there are a lot of good website security techniques that can be used, because there is a LOT to website security.
– Great article, and deserves to (actually, SHOULD BE) added to everyone’s list of important bookmarks.
– Jim
Thanks Jim for the lengthy and extremely useful comment. Great idea regarding the WP security. I will try that one out.
All the best
Jamie
Great suggestions. Curious about your thoughts on combining security plugins like Wordfence or iThemes with manual tweaks like changing permissions or wpconfig location– do those two things interfere with each other? I’ve noticed that, for example, Wordfence doesn’t like competing with other security plugins, so wasn’t sure if it also wouldn’t play nice with those sorts of manual changes?
I have to agree with you there Stephen. I too have to make manual tweaks to the config file. It seems to work ok, although I do think that there is room for improvement in terms of a product that offers complete compatibility.